Sonar visualizes your Salesforce event monitoring data, enabling Revenue Operations & Systems leaders to proactively monitor integrated system access, observe anomalies in API consumption and stay ahead of potential data leaks.
Giving Life to Your Salesforce Event Monitoring Data
For businesses dedicated to Salesforce data security, an essential investment to your data governance program should be in Salesforce’s data monitoring & end-to-end encryption product, Salesforce Shield. Salesforce Shield arms Systems, Ops & InfoSec teams with a trio of security tools built to protect business sensitive data and PII. But post-purchase, many Salesforce operations teams find themselves struggling to realize the full potential of Shield’s event monitoring feature.
Meet Pulse. Salesforce Shield’s New Best Friend.
Sonar Pulse analyzes and interprets your event monitoring access logs in real-time, then visualizes the integrated applications connecting to Salesforce on our always-on Pulse dashboard. Revenue Operations and Systems owners depend on Sonar’s tech stack diagram to detect newly connected applications, monitor for changes to known applications, and observe API activity for capacity planning and anomaly detection.
Breakages happen silently.
Too often, integration breakages are detected and reported by end users after considerable damage has already occurred. Business systems owners are found reactively addressing issues rather than proactively planning and monitoring integrations to meet SLOs and keep sensitive data secure. Sonar Pulse monitors your known applications, notifying you when field and object level access changes occur.

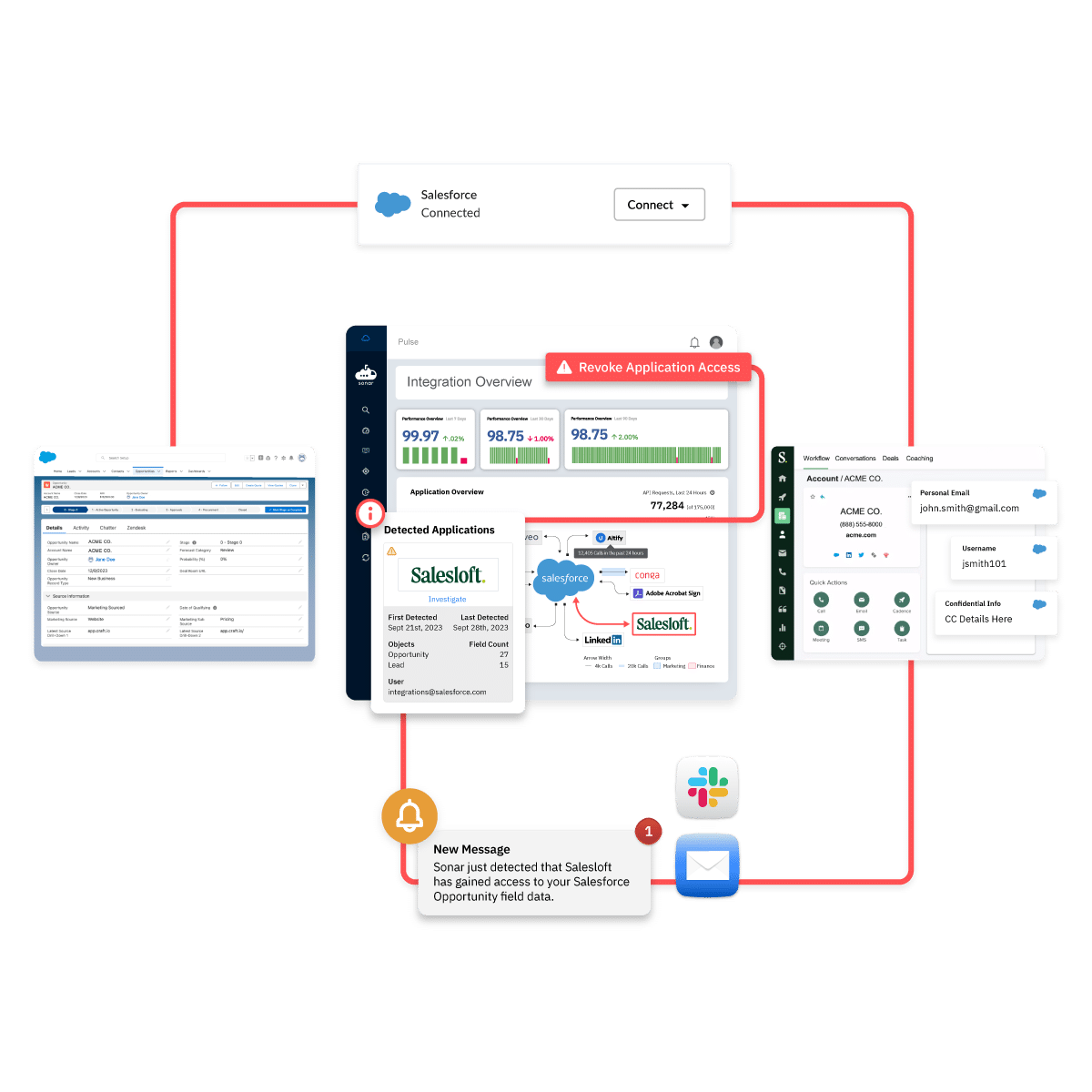
Almost anyone can connect to a new application.
Many SaaS applications now offer one-click integration to Salesforce, meant to simplify GTM team workflows. But these can unknowingly open the door to data leakage and other security risks. Sonar instantly detects when a new application gains access to Salesforce, providing email alerts and Slack notifications to business stakeholders. From our Pulse dashboard, Salesforce owners can review comprehensive logs to understand how the new system is interacting and can even revoke application access with a single click.
Duplicate and abandoned integrations can be expensive.
With a rapidly expanding tech stack, it’s easy to overlook duplicate and abandoned integrations. Even when you think you’ve disconnected a legacy technology, you may be surprised to know that API access calls are still occurring. Sonar gives Operations an easy to read tech stack diagram, grouping integrations by department and business purpose to spot redundant technologies, integration tech debt, and ensure Salesforce data security.
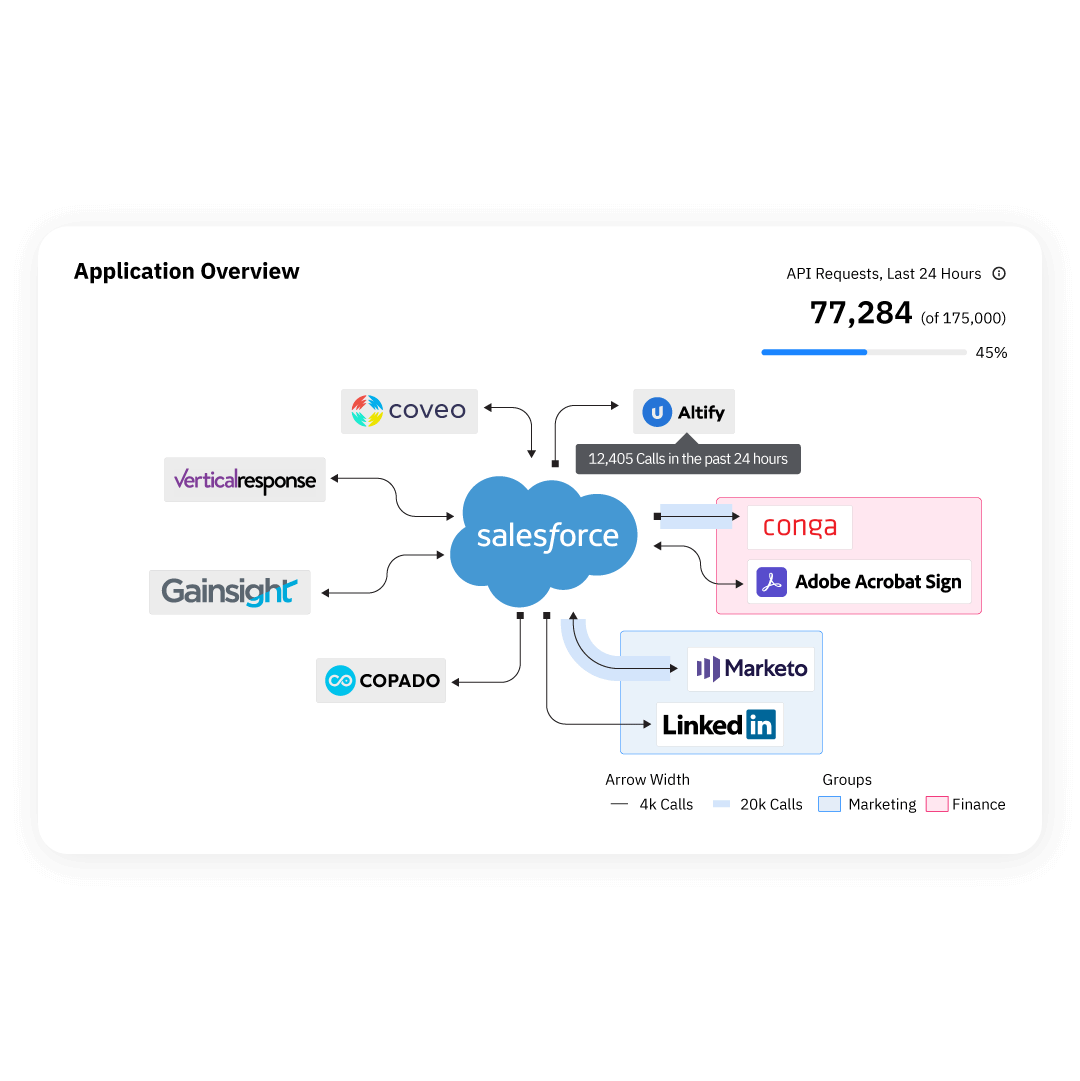
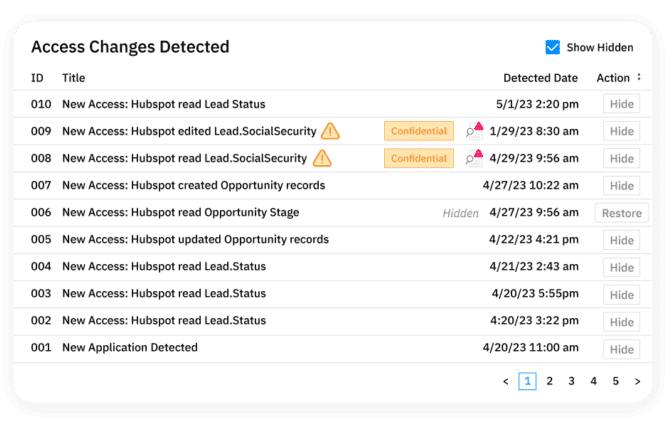
Manage incidents effectively.
When access changes occur or service anomalies are detected, Sonar arms business leaders with detailed, easy to interpret access logs that can be filtered by user, field name, parent object and data classification. Sonar can even generate case-specific remediation plans to guide you through your investigation.
Maximize the Value of Salesforce Shield, with Sonar
Sonar’s observability and monitoring software allows smart business leaders to maximize their investment in Salesforce Shield, helping to elevate Salesforce security and productivity.