Data loss at any level comes with some serious consequences for businesses. But when it comes to organizations managing sensitive and personal client information— you might be regulated under one of the most strict privacy regulations around– the Health Insurance Portability and Accountability Act (HIPAA). And violating this regulation in particular comes with even larger consequences– we’re talking up to hundreds of thousands of dollars in fines or even potential imprisonment.
But we’re not here to be fear mongers. We’re here to help fill in a blind spot that Systems leaders may not have thought about– their Salesforce CRM. Sure, you may have the Healthcare Cloud and think you’re covered. But there’s still ways for your Salesforce to pose potential risks.
Below, we’re covering everything InfoSec leaders need to know about HIPAA compliance, how it impacts the way you and RevOps manage your Org, and how to safeguard the Protected Health Information (PHI) in one of your most critical business systems.
What is HIPAA Compliance?
HIPAA is a federal law that mandates the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge. Compliance with HIPAA involves adhering to standards set forth in the Privacy Rule, the Security Rule, and the Breach Notification Rule.
1. Privacy Rule
The Privacy Rule establishes national standards for the protection of PHI. This rule applies to health plans, healthcare clearinghouses, and healthcare providers that conduct certain healthcare transactions electronically. It requires covered entities to implement safeguards to protect patient privacy and sets limits and conditions on the uses and disclosures of PHI without patient authorization. It grants patients rights over their health information – including rights to examine and obtain a copy of their health records and request corrections.
2. Security Rule
The Security Rule specifies a series of administrative, physical, and technical safeguards for covered entities to ensure the confidentiality, integrity, and security of electronic PHI (ePHI). This includes requirements for risk assessment and management, workforce training, and the implementation of policies and procedures designed to limit access to, and protect, ePHI. The Security Rule is flexible, allowing covered entities to tailor their security measures to their size, operations, and the nature of the ePHI they handle.
3. Breach Notification Rule
HIPAA compliance is critical for several reasons beyond the legal obligation to protect patient health information. It fosters trust between patients and healthcare providers, ensures the secure handling of sensitive data in an increasingly digital world, and protects healthcare entities from the reputational damage and financial penalties associated with data breaches and non-compliance. For organizations handling PHI, achieving and maintaining HIPAA compliance is not just a regulatory requirement but a fundamental component of ethical responsibility and patient care.
Entities That Must Comply with HIPAA
How do you know if your business or practice must comply with HIPAA? According to the privacy regulation, compliance is required for any entities that handle PHI. These entities are broadly categorized into two main groups: Covered entities and business associates. Here’s a closer look at who needs to be compliant and examples of each:
Covered Entities
Covered Entities are the main actors in the healthcare sector who are directly involved in the treatment, payment, and operations in healthcare. They include:
1. Healthcare providers: This group includes doctors, clinics, psychologists, dentists, chiropractors, nursing homes, and pharmacies. However, it’s important to note that for healthcare providers to be considered covered entities, they must conduct certain transactions in electronic form, such as submitting claims to health plans.
2. Health plans: Health plans encompass health insurance companies, HMOs (Health Maintenance Organizations), company health plans, and government programs that pay for healthcare, such as Medicare, Medicaid, and the military and veterans’ healthcare programs.
3. Healthcare clearinghouses: These entities process nonstandard health information they receive from another entity into a standard (electronic or otherwise) or vice versa. Examples include billing services and community health management information systems.
Business Associates
Business associates are persons or entities that perform certain functions or activities that involve the use or disclosure of PHI on behalf of, or provide services to, a covered entity. A business associate’s services to a covered entity are limited to legal, actuarial, accounting, consulting, data aggregation, management, administrative, accreditation, or financial services.
Examples include:
- Data processing firms or healthcare technology companies: Entities that provide software as a service (SaaS) that involves processing, storing, or transmitting PHI.
- Document and records storage or destruction companies: Companies that handle the storage or shredding of PHI records.
- Third-party administrators: That assist in the administration of health plans.
- Consultants: Who perform utilization reviews for hospitals.
- IT service providers: That manage the security of ePHI such as cloud hosting services.
- Billing companies: That manage billing for healthcare providers.
- Law firms: If they have access to PHI when providing legal services to a covered entity.
- EHR (Electronic Health Record) vendors: If they are hosting or have access to PHI.
- Subcontractors: Additionally, subcontractors and other business associates of business associates who have access to PHI also must be compliant with HIPAA regulations. This extension ensures that all layers of contact with PHI are covered by HIPAA’s protective measures.
HIPAA compliance is required for a broad spectrum of entities in the healthcare ecosystem, from those providing care directly to patients to those handling PHI in a supportive role. Ensuring compliance across these entities is crucial for the protection of sensitive health information.
Key Requirements for HIPAA Compliance
HIPAA compliance represents a comprehensive approach to protecting patient privacy and securing health information. It requires a continuous commitment from covered entities and their business associates to adhere to the evolving standards and practices set forth by HIPAA.
But remaining compliant is no easy feat for practices… it requires numerous steps for your security, Ops, and GTM teams alike. Here’s a list of requirements your organization must adhere to:
1. Privacy rule compliance
Ensuring the confidentiality of PHI, including provisions for patient rights to access and control their own health information.
2. Security rule compliance
Implementing technical, physical, and administrative safeguards to ensure the confidentiality, integrity, and security of ePHI.
3. Breach notification rule compliance
Establishing procedures for responding to breaches of PHI, including notifications to affected individuals, the Department of Health and Human Services (HHS), and sometimes the media.
4. Conducting regular risk assessments
Identifying potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI and implementing security measures to mitigate these risks.
5. Employee training and awareness
Providing ongoing training to all employees about their roles in protecting PHI and ensuring they understand HIPAA requirements.
6. Data encryption
Encrypting PHI both at rest and in transit to prevent unauthorized access.
7. Access controls
Restricting access to PHI to only those employees who need it for their job functions.
8. Audit controls
Implementing mechanisms to record and examine access and other activities in information systems containing PHI.
9. Physical security
Implementing physical safeguards for all areas where PHI is stored or accessed, to protect against unauthorized access, tampering, and theft.
10. Incident response plan
Developing and maintaining an incident response plan for addressing and responding to security incidents that impact the confidentiality, integrity, or availability of PHI.
11. Business associate agreements (BAAs)
Executing BAAs with third-party vendors who have access to PHI, ensuring they comply with HIPAA regulations.
12. Policies and procedures documentation
Developing and maintaining written policies and procedures that comply with HIPAA standards and retaining necessary documentation.
13. Patient rights
Ensuring procedures are in place to address patient rights such as accessing their PHI, requesting amendments, and receiving an accounting of disclosures.
14. Secure communication channels
Ensuring secure and compliant communication channels for transmitting PHI, such as secure messaging platforms and email encryption.
15. Disposal of PHI
Implementing secure methods for disposing of PHI when no longer needed, including shredding paper records and securely erasing electronic files.
16. Regular compliance audits and reviews
Conducting periodic audits to assess HIPAA compliance and adjusting policies and procedures as necessary.
17. State law compliance
Adhering to state laws regarding the protection of health information, which may be more stringent than federal regulations.
Consequences of Violating HIPAA
The consequences of a HIPAA violation can be severe, affecting both the violating entity and the individuals whose PHI has been compromised. These consequences are designed to enforce compliance and protect patient privacy. They can be categorized into civil and criminal penalties, along with reputational damage:
1. Civil Penalties
Civil penalties for HIPAA violations are tiered based on the nature of the violation and the level of negligence involved. The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) determines the penalty amount, which can range significantly:
- Tier 1: Violations where the entity was unaware and could not have realistically avoided, had a reasonable amount of care been taken to abide by HIPAA Rules. The penalty ranges from $100 to $50,000 per violation, with an annual maximum of $25,000 for repeat violations.
- Tier 2: Violations that have a reasonable cause and not due to willful neglect. Penalties range from $1,000 to $50,000 per violation, with an annual maximum of $100,000 for repeat violations.
- Tier 3: Violations due to willful neglect but the violation was corrected within the required time period. The penalty ranges from $10,000 to $50,000 per violation, with an annual maximum of $250,000 for repeat violations.
- Tier 4: Violations of willful neglect that were not corrected. Penalties can go up to $50,000 per violation, with an annual maximum of $1.5 million.
2. Criminal Penalties
Criminal penalties are handled by the Department of Justice (DOJ) and can be more severe, including fines and imprisonment. These penalties are based on the severity of the violation and the intent:
- Unknowing violation: Up to $50,000 in fines and one year of imprisonment.
- Violation under false pretenses: Up to $100,000 in fines and up to five years in prison.
- Violation with intent to sell, transfer, or use PHI for personal gain, harm, or commercial advantage: Up to $250,000 in fines and up to ten years in prison.
3. Reputational Damage
Beyond the civil and criminal penalties, HIPAA violations can cause significant reputational damage to organizations. The public disclosure of a HIPAA breach can lead to loss of trust among patients and partners, potentially resulting in a loss of business and decreased profitability. Organizations may also face lawsuits from individuals affected by the breach.
4. Corrective Actions
In addition to penalties, entities found in violation of HIPAA may be required to undertake corrective action plans to address and remedy the compliance issues. These plans often include extensive reporting requirements to HHS for a period of time, further training of staff, and significant changes to policies and procedures regarding the handling of PHI.
The consequences of HIPAA violations highlight the importance of compliance and the need for entities handling PHI to implement robust privacy and security measures. Regular training, risk assessments, and adherence to HIPAA regulations are critical steps in protecting patient information and avoiding these penalties.
It may also require InfoSec leaders to take a deeper look at their tech stack– especially their Salesforce org which likely connects with numerous third-party tools.
How Salesforce Fits Into Your HIPAA Compliance Program
Having established the fundamental requirements for HIPAA compliance, it’s essential to pivot our focus towards how specific technologies, particularly Salesforce, fit into this framework.
As a leading CRM platform, Salesforce often serves as the repository for a vast amount of sensitive health information. Ensuring data classification of Salesforce metadata is critical for HIPAA compliance. And this level of involvement requires you as the Systems Lead or Ops lead to have a holistic view of your Org. It’s key to know exactly where data is, who’s accessing it and how it’s being used.
If you don’t know the answer to the following questions, odds are you’re not in compliance. But third-party tools like Sonar might help fill in the gaps. Check it out:
1. Where is data being stored?
Documentation of Salesforce metadata is important for HIPAA compliance. It includes details about how data is handled, processed, and protected within Salesforce. Creating a Salesforce data dictionary that includes a list of the fields, integrations and other elements that store or have access to sensitive data is foundational first step. This documentation serves as a record of compliance efforts and is crucial during audits. Organizations need to regularly update and maintain this documentation to reflect any changes in Salesforce configurations or processes.
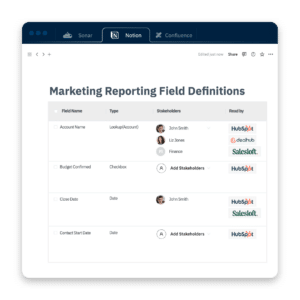
Pro tip: Elevate Salesforce data governance policies with Sonar
Sonar’s Data Dictionary feature helps IT, Ops and Business Systems leaders adhere to internal data governance programs by simplifying data classification. Ensure Salesforce information security by documenting data sensitivity levels, classifying where Personal Identifiable Information (PII) may be stored and even how and where it is being accessed across your integrated tech stack.
2. Who has access to your data?
Controlling who has access to PHI within Salesforce is vital. This is managed by setting up user profiles and permission sets. Collaborating with your RevOps teams to develop appropriate profiles and permission sets is essential. This ensures that only authorized personnel have access to sensitive data, aligning with the ‘Minimum Necessary’ rule of HIPAA for data access.
3. How is data kept private?
Salesforce offers robust data storage solutions with a focus on security and compliance. A key feature is Salesforce Shield Encryption, which encrypts sensitive data. This encryption ensures that such data is not viable or accessible by unauthorized users. Organizations must leverage this feature to protect PHI and comply with the encryption requirements of HIPAA.
4. Is data being accessed by other systems?
Understanding the integration of Salesforce with other systems is key to maintaining HIPAA compliance. It’s important to know who has access to these systems and how they interact with PHI within Salesforce. The Event Monitoring feature in Salesforce can be instrumental in tracking access to Salesforce data by other systems. This feature allows organizations to monitor and record all access, providing visibility and control over external system interactions.
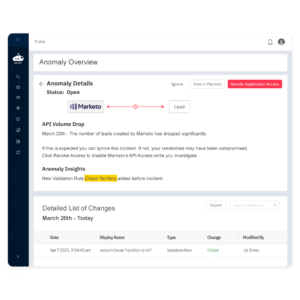
Pro tip: Implement integration monitoring with proactive threat detection
Sonar’s Event Monitoring data loss prevention software detects changes to application access and permissions and alerts Ops, IT and InfoSec leaders when business sensitive data leakage may be at risk. This tool allows you to have a proactive approach to event monitoring and data leakage as opposed to the traditional, reactive model most teams are working off of.
5. How are you reporting and documenting incidents?
In the event of a security incident, it’s crucial to have efficient tracking and reporting mechanisms in Salesforce. Utilizing audit trails and data logs within Salesforce helps in documenting and analyzing incidents. These records are vital for proving that the incident has been effectively managed and resolved. They also assist in developing action plans to prevent future occurrences and demonstrate compliance with HIPAA’s breach notification and incident response requirements.
Pro tip: Manage incidents effectively with Sonar
When outages occur, Sonar instantly alerts and arms business systems leaders with detailed and up-to-date information regarding the incident — from performance metrics, SLAs, related automations and fields, and underlying infrastructure to system stakeholders, owners and the documentation required to resolve issues quickly.
Conclusion: Get a Holistic View of Your Salesforce Org to Ensure HIPAA Compliance
Having a big-picture view of your Salesforce and its integrated tech stack is critical to remaining compliant with HIPAA. The responsibility of remaining compliant within your Org can’t solely rely on InfoSec— with Ops and GTM teams utilizing the tool, it must be a collaborative and shared responsibility.
Sonar makes overseeing PHI simple. Our all-in-one Salesforce solution provides InfoSec teams:
- Event monitoring across your GTM tech stack
- Simplified salesforce data classification
- Change logs for Salesforce audits
- Mitigated risk and ensured system uptime
And more. Implement Sonar for strengthened HIPAA compliance today. Click here to get started for free.

