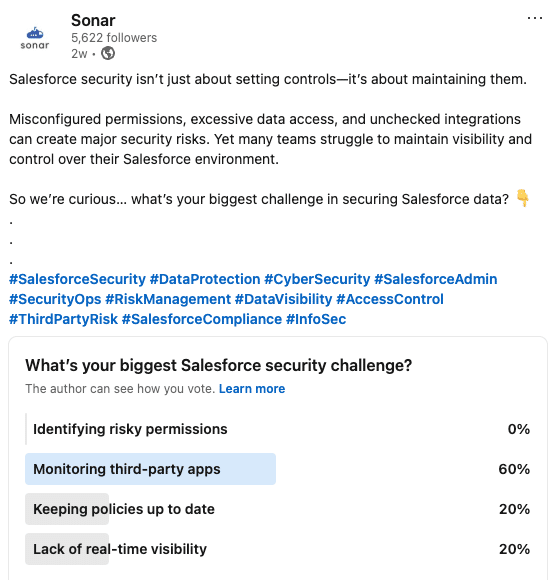
APIs power Salesforce integrations, seamlessly connecting your CRM with third-party apps to automate workflows and drive efficiency. But with great connectivity comes great risk. Mismanaged API access can lead to data breaches, compliance violations, and operational disruptions—yet many orgs unknowingly leave their APIs exposed due to overly permissive settings and poor access controls. In fact, 60% of security practitioners cite secure API access as one of their biggest challenges, highlighting the growing concern around unauthorized data exposure.
With AI-driven tools increasing API reliance, securing your endpoints is more critical than ever. So how can you protect sensitive data without disrupting business operations? In this guide, we’ll cover best practices for API security, from monitoring and access restrictions to proactive threat detection.
The Top Concerns Security Leaders Have When Securing Salesforce APIs
Salesforce API security isn’t just about managing access—it’s also about staying ahead of evolving threats. Misconfigurations, unchecked integrations, and increasingly sophisticated cyberattacks can all put sensitive data at risk. So what keeps security leaders up at night when it comes to API security? Let’s break down the top concerns and how to address them.
1. Expanding Attack Surface
Salesforce APIs are designed for flexibility, enabling seamless integrations across your tech stack. But with every new connection—whether it’s a marketing automation platform, an AI-powered analytics tool, or a custom-built app—the attack surface grows. Each API endpoint represents a potential entry point for bad actors, making it crucial to monitor and control access at all times.
One major challenge is shadow integrations—third-party apps or services connected to Salesforce without security oversight. Employees often grant API access to tools for convenience, but without visibility into these integrations, security teams have no way to assess their risk.
Additionally, overly permissive API settings can leave sensitive data exposed. Many orgs default to broad access permissions, allowing applications to read, write, or extract data beyond what’s necessary. This not only increases the risk of unauthorized access but also makes detecting malicious activity harder.
2. Prevalence of Security Issues
API attacks are skyrocketing—84% of security professionals reported an API security incident in the past 12 months, marking an all-time high. Many of these breaches stem from misconfigurations, weak authentication, and excessive data exposure. As organizations scale their Salesforce integrations, security gaps often go unnoticed until an attack occurs.
One major risk is insecure API keys and tokens. When credentials are hardcoded in applications, improperly stored, or left exposed in public repositories, attackers can easily exploit them to access Salesforce data. Weak authentication methods—such as relying solely on API keys instead of OAuth and multi-factor authentication (MFA)—further increase the risk of unauthorized access.
Another widespread issue is excessive data exposure. Many APIs return more information than necessary, making data leaks more likely if an endpoint is compromised. Without strict controls over what data is accessible and how it’s shared, even a minor oversight can lead to significant security incidents.
3. More Sophisticated Threats
Attackers are constantly evolving, and Salesforce APIs are no exception. Threat actors are moving beyond basic credential stuffing and misconfiguration exploits—now leveraging AI-powered attacks, API abuse, and supply chain vulnerabilities to gain access to sensitive data. As security teams work to close traditional gaps, attackers are developing more advanced tactics to bypass defenses.
One emerging threat is API abuse and business logic attacks. Instead of directly exploiting a vulnerability, attackers manipulate API workflows as intended but for malicious purposes—such as exploiting overly permissive permissions to extract massive amounts of data without triggering security alerts. Automated bot attacks also pose a growing concern, using stolen credentials or brute-force techniques to gain persistent access to Salesforce APIs.
Additionally, AI-driven threats are accelerating attack sophistication. Cybercriminals are using AI to identify weak points in Salesforce API security, generate realistic phishing attempts targeting API credentials, and automate large-scale attacks at unprecedented speed. Third-party supply chain risks further complicate security, as attackers increasingly target connected applications with weaker defenses as an entry point into Salesforce.
Best Practices for Salesforce API Security
With API threats evolving, security teams need more than just basic protections—they need continuous oversight, strict access controls, and proactive risk mitigation. Implementing a strong security framework ensures that Salesforce APIs remain both functional and secure without exposing sensitive data to unnecessary risks.
1. Enforce Strong Authentication
One of the most critical steps in ensuring Salesforce API security is enforcing strong authentication. Organizations should require OAuth 2.0 for all API connections rather than relying on static API keys, which are more vulnerable to theft and misuse. Multi-factor authentication (MFA) should also be enforced wherever possible to add an extra layer of security, preventing unauthorized access even if credentials are compromised. Additionally, implementing IP whitelisting and device-based restrictions helps limit API access to only approved locations and users, reducing the risk of malicious activity.
2. Limit Data Exposure
Many APIs return more data than necessary, increasing the risk of leaks if an endpoint is misconfigured or exploited. By applying the principle of least privilege, organizations can ensure that APIs only have access to the specific data they need to function. Field-level security should also be configured to restrict sensitive information based on user roles, preventing unauthorized access to critical business data.
3. Monitor API Activity in Real Time
Real-time monitoring plays a crucial role in identifying potential security threats before they escalate. Organizations should implement API monitoring tools that track usage patterns and detect unusual activity, such as excessive data extraction or unauthorized integrations. Setting up alerts for anomalies enables security teams to respond quickly to potential breaches, minimizing damage. Maintaining comprehensive audit logs also helps with forensic investigations and compliance reporting.
 4. Secure API Credentials
4. Secure API Credentials
API credentials must be carefully managed to prevent unauthorized access. Storing API keys and tokens securely using secrets management tools helps reduce the risk of exposure. Regularly rotating these credentials further minimizes the chances of attackers exploiting outdated or leaked keys. Hardcoding API credentials in applications should be strictly avoided, as this increases the risk of accidental exposure in public repositories or code leaks.
5. Prevent API Abuse & Automated Attacks
Preventing API abuse requires additional safeguards to block automated threats. Implementing rate limiting helps prevent malicious actors from launching brute-force attacks or scraping large amounts of data. Organizations should also deploy bot mitigation solutions to identify and block automated threats targeting API endpoints. Restricting API access based on IP addresses or geographic locations further reduces the attack surface.
6. Conduct Regular Security Audits
Organizations should conduct regular security audits and penetration testing to identify vulnerabilities before attackers can exploit them. Routine assessments help uncover misconfigurations, excessive permissions, and other security gaps that may otherwise go unnoticed. Staying up to date with Salesforce security patches and best practices ensures that APIs remain protected against emerging threats.
How to Detect and Mitigate API Security Threats
Keeping your Salesforce APIs secure isn’t just about setting up access controls. It’s also about staying vigilant and catching threats before they turn into full-blown breaches. Hackers and insiders can exploit APIs to extract sensitive data or gain unauthorized access, making proactive monitoring a must.
By watching for unusual patterns and tracking data flows, your team can detect suspicious activity early and take swift action. Let’s explore some key areas to focus on when monitoring for API security threats.
1. Unusual API Activity
If something looks off, it probably is. A sudden spike in API calls or access attempts from unknown IP addresses could signal an attempted breach. Attackers often test API endpoints to find weaknesses, and if your system isn’t closely monitored, these attempts might go unnoticed until it’s too late.
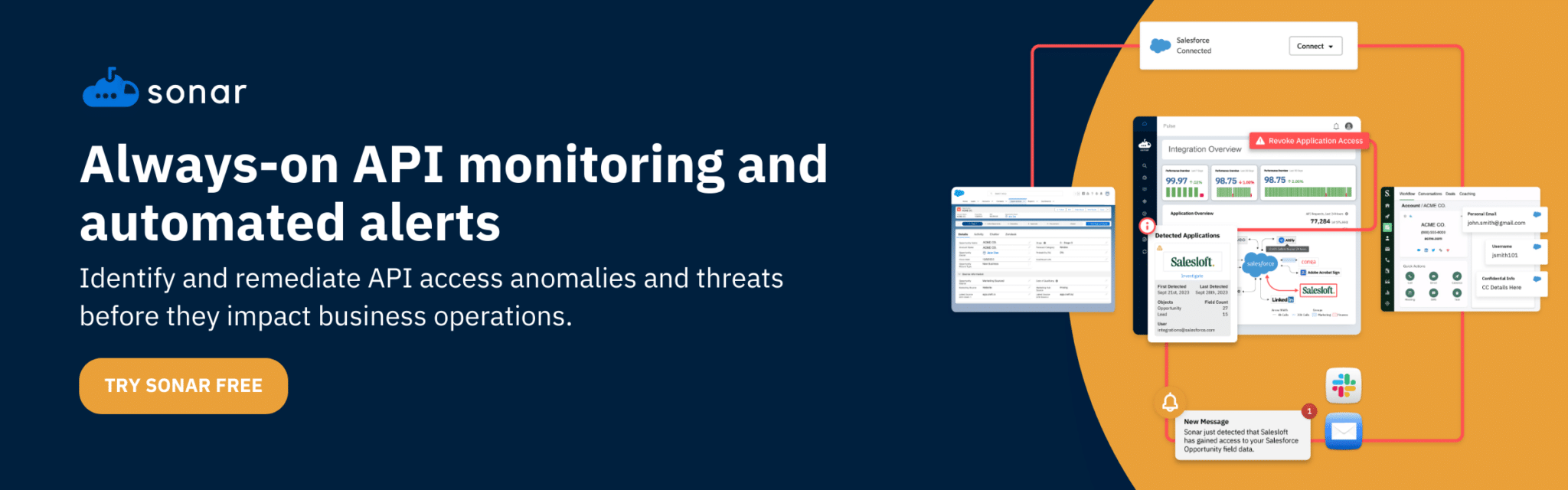
Setting up alerts for unusual API activity, such as excessive login failures, unexpected request volumes, or access from unfamiliar geolocations, helps your team catch potential threats early. With Sonar’s pre-built dashboards, your security team can instantly spot anomalies in API activity, helping you investigate and respond to suspicious behavior before it escalates.
 2. Data Exfiltration Risks
2. Data Exfiltration Risks
APIs are a common target for data thieves looking to move large amounts of sensitive information out of your Salesforce environment. Massive data transfers, especially outside of normal business hours or from unknown integrations, should raise red flags. Attackers might exploit weak access controls to siphon off customer data, financial records, or intellectual property without triggering alarms, unless you’re actively monitoring for it.
To prevent data exfiltration, set limits on API data exports, monitor for unusually high data transfer volumes, and implement data loss prevention (DLP) policies that flag potential unauthorized access attempts. Limiting the amount of data that can be accessed in a single API call can also reduce the impact of potential breaches.
By taking a proactive approach to API security, you can significantly reduce the risk of unauthorized access and data loss. With tools like Sonar, your team can gain real-time visibility into API activity, quickly detect threats, and stay ahead of potential security issues.
Conclusion: Stay Ahead of API Security Challenges with the Right Tools
Securing your Salesforce APIs is crucial for protecting sensitive data, staying compliant, and ensuring your integrations run smoothly without unnecessary risks. By taking a proactive approach – implementing strong access controls, monitoring API activity, and regularly reviewing permissions – you can safeguard your Salesforce environment against potential threats.
But staying on top of it all doesn’t have to be overwhelming. With Sonar, you get real-time monitoring, actionable insights, and instant alerts to help you detect and respond to API security risks with confidence.
Ready to simplify your API security? Try Sonar free today.