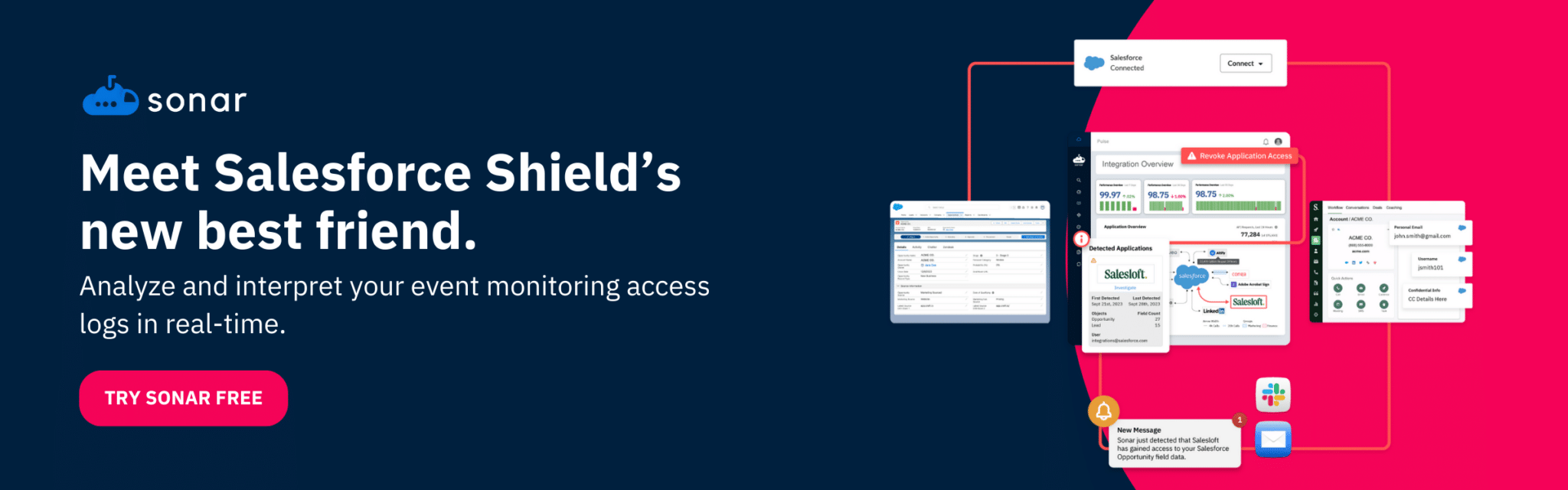
Do you feel like your team has loads of data at their fingertips and yet you’re still starved for real insights?
While Salesforce Shield offers crucial visibility into user actions and data access, harnessing its full power is challenging. Complex logs make it hard to pinpoint real threats quickly, often leaving teams reacting to incidents rather than preventing them.
Factor in high costs and the strain on resource-stretched admins, and it’s easy for Security and Ops teams to wonder… What’s the point in investing in aggregating event data if we have no way to act on it?
The truth is, that when optimized, Shield is a game-changer. Unlocking its event monitoring capabilities allows your team to better protect Salesforce data and reduce IT costs by up to 25%. In this blog, we’ll explore the main challenges with Salesforce Shield Event Monitoring and provide actionable strategies to transform these obstacles into security successes.
Mitigating Key Challenges of Salesforce Shield Event Monitoring
While Salesforce Shield offers essential visibility into your Salesforce environment, making it truly effective requires navigating some complex challenges. From extracting data in a usable format to interpreting abstract insights, each step demands a thoughtful approach to ensure Event Monitoring serves your organization effectively.
By addressing these challenges head-on, teams can transform Shield Event Monitoring from a reactive tool into a proactive security asset. Let’s explore common hurdles and offer practical solutions to help your team leverage Shield’s capabilities for stronger security, streamlined operations, and enhanced compliance.
1. Challenge: Navigating the Complexity of Event Monitoring Logs
Before taking a look at the full potential of Salesforce Shield, it’s crucial to address one of the biggest roadblocks: the complexity of Event Monitoring logs.
Salesforce Shield produces a vast volume of data, tracking everything from user activity to API calls. While this data is invaluable for security, its sheer volume and complexity can quickly leave teams feeling overloaded. Without a clear, structured way to interpret these logs, making timely, data-driven security decisions is challenging. For many, parsing out meaningful insights from this flood of information is a daily struggle. Yet, conquering this complexity is crucial to ensure fast, effective responses to security threats.
Let’s explore how to simplify and streamline log data, transforming it into actionable insights that drive security outcomes.
Solution
- Data Visualization and Alerts: Tools like Sonar simplify Salesforce Shield’s Event Monitoring logs by translating raw data into clear, visual dashboards. These dashboards highlight key trends and anomalies, helping teams quickly identify unusual activity and prioritize security risks. Automated alerts further streamline this process, instantly notifying teams of suspicious actions, such as unexpected logins or data exports, so they can respond promptly and efficiently.
- Filtering and Aggregating Log Data: Salesforce Shield users can utilize filtering and aggregation tools within Shield or with data analysis platforms to refine logs down to the most relevant information. By filtering out routine events and focusing on anomalies or high-risk activities, teams can eliminate noise, making it easier to spot meaningful patterns.
- Scheduled Data Summaries and Automated Reporting: To reduce the manual load, teams can automate scheduled data summaries and reports, which highlight critical metrics and unusual trends over time. Regular, automated reports keep teams updated without needing constant log-checking and help in spotting shifts that may indicate emerging threats.
- Proactive Threshold-Based Alerts: Setting custom thresholds for specific activities, such as the number of failed logins or volume of data exports, can provide early warnings of potential threats. Teams receive alerts only when activities exceed these thresholds, enabling a more proactive, prioritized response to potential risks while reducing alert fatigue.
2. Challenge: Integration Fatigue Among Ops Teams
Once teams overcome the complexity of interpreting event monitoring logs, they often face another obstacle: integration fatigue. For many Ops and admin teams, the thought of adding Salesforce Shield’s monitoring capabilities to an already intricate tech stack can be daunting, with concerns about setup complexity, potential workflow disruptions, and the time required to manage new integrations.
This fatigue can discourage teams from fully leveraging Shield’s capabilities, limiting the platform’s effectiveness and weighing down resources. Without streamlined integration, teams may become bogged down by setup requirements, ongoing maintenance, and compatibility issues that detract from higher-priority security initiatives.
To unlock the full value of Shield without exhausting resources, it’s essential to adopt tools and processes that make integration seamless and maintain an efficient, cohesive workflow across systems.
Solution
- Automation and Centralization with Sonar: An observability platform like Sonar eases integration fatigue by centralizing Salesforce monitoring and automating routine tasks. By consolidating data and alerts into a single, unified view, Sonar simplifies workflows, accelerates insights, and frees up teams to focus on strategic priorities. This centralized approach transforms event monitoring into an efficient, seamless process that complements daily operations.
- Native Integrations and API Management: Leveraging native integrations with Salesforce-compatible tools can minimize integration complexity and reduce maintenance requirements. By choosing solutions that work directly with Salesforce’s APIs, teams avoid the added burden of custom development and maintenance, ensuring that Shield’s monitoring capabilities work in harmony with other systems.
- Batch Processing and Data Sync Schedules: Scheduling batch processing or periodic data syncs for lower-priority monitoring tasks can reduce the constant data flow into your tech stack, allowing teams to process less critical data at designated intervals. This approach helps balance system load, improving performance and reducing fatigue from constant alerts.
- Automated Alerts and Reporting: Automation doesn’t have to be complex. Automating alerts for high-priority activities and setting up regular reports on key metrics can keep Ops teams updated on critical events without the need for constant log-checking. Automated reports ensure fresh, actionable insights without manual compilation, helping teams stay proactive and focused on high-impact security tasks.
3. Challenge: Balancing Security with Business Continuity
After addressing integration fatigue, teams face another critical challenge: balancing robust security measures with the need for uninterrupted business operations. Striking this balance is essential, as overly restrictive security settings can hinder productivity, while lenient configurations may expose sensitive data to risk.
Achieving a secure yet seamless Salesforce environment requires strategies that protect data without compromising business continuity. Let’s explore how to maintain this balance.
Solution
- Real-Time Monitoring and Resource Optimization with Sonar: Sonar offers real-time monitoring of key metrics, such as API call usage and system resource limits, which can help teams proactively manage resource allocation. With this visibility, Ops teams can monitor potential bottlenecks and adjust configurations before they impact productivity. Sonar analyzes access log data, benchmarking expected behavior and providing alerts only when deviation occurs. These monitors allow for optimized resource planning, enabling smooth, continuous operations without compromising security.
- Cross-Departmental Collaboration: To align security measures with business needs, Ops teams should collaborate closely with departments like sales, customer service, and Infosec. By working together, teams can ensure security policies support day-to-day workflows and avoid disruptions. Regular feedback loops with department leaders can help refine policies, ensuring that both productivity and security requirements are met.
- Automated Threshold Alerts for Business-Critical Processes: Setting automated threshold alerts for specific activities—such as data exports or high-frequency logins—allows teams to proactively manage unusual events without manually monitoring every action. This approach helps identify potential threats that could disrupt business operations, so they can be addressed before escalating into larger issues.
4. Challenge: Ensuring Compliance with User and API Monitoring
Once you strike a balance between security and business continuity, the next priority is effective user and API monitoring to meet compliance standards such as GDPR, HIPAA, and PCI DSS. For security leaders, maintaining ongoing compliance is a top priority, yet it can be difficult to continuously track and identify unauthorized access.
While Salesforce Shield’s event monitoring provides key visibility into access behavior, it requires a structured approach to reliably meet regulatory requirements. Let’s take a look at strategies to tackle this compliance challenge.
Solution
- Proactive Monitoring and Automated Incident Response with Sonar: Sonar provides real-time alerts for potential security breaches and access anomalies, allowing teams to respond immediately to compliance risks. This proactive approach prevents data exposure incidents that could lead to regulatory violations and helps keep sensitive information secure. Additionally, Sonar’s automated auditing capabilities streamline compliance reporting by analyzing Shield’s field audit trails and generating ready-to-use reports, minimizing manual audit tasks and helping teams stay audit-ready with ease.
- Routine Access Reviews and User Behavior Analytics: Regularly reviewing access permissions helps ensure that users have only the level of access necessary for their roles, which is crucial for compliance. Combining this with user behavior analytics (UBA) allows teams to spot unusual patterns or behaviors that may signal compliance risks, such as high-frequency logins or unauthorized data exports.
- Automated Reporting for Compliance Readiness: Automating compliance reporting can further simplify audit preparation. By setting up automated reports for key compliance metrics and monitoring trends over time, security teams can ensure they always have up-to-date insights into compliance posture. This also reduces the time and effort required to compile data during audits, enabling faster responses to regulator requests.
- Role-Based Access and Policy Controls for Data Privacy: Leveraging role-based access controls and establishing data policies aligned with compliance standards can reduce exposure risks. Tailoring permissions to specific roles and implementing restrictions on sensitive data access—especially in high-risk areas like customer information—ensures that data handling aligns with regulatory requirements.
5. Challenge: Gaining Organizational Buy-In for Salesforce Shield
Gaining organizational buy-in for Salesforce Shield can pose a challenge all on its own. Security initiatives like the integration of Shield can encounter resistance, primarily due to its perceived complexity and cost.
Additionally, when stakeholders don’t fully understand the specific risks that Shield mitigates, it can be difficult to make a compelling case for prioritizing it. Securing this buy-in is crucial for creating Salesforce environments that are properly safeguarded and that security measures receive the support they need to be effective.
Let’s dive into strategies for communicating the value of Shield to leadership and building organization-wide support.
Solution
- ROI Communication: One of the most effective ways to gain buy-in for Salesforce Shield is by framing it as a cost-saving and risk-reduction tool, rather than just a security expense. Security leaders can present Shield’s value by quantifying the potential cost of data breaches, compliance violations, and reputational damage. By emphasizing Shield as a long-term investment in risk management and cost efficiency, stakeholders are more likely to recognize its strategic importance.
- Enhanced Visibility and Reporting Tools: A variety of platforms, including Sonar, offer visibility tools that make it easier for leadership to appreciate the real-time impact of Shield. Sonar’s dashboards, for example, translate complex monitoring data into easy-to-understand metrics, demonstrating Shield’s contributions to data protection and compliance. Similar visibility tools can provide stakeholders with clear, measurable indicators of Shield’s benefits, helping them see its impact on data security and compliance at a glance.
- Regular Reporting with Measurable Outcomes: Establish regular reports or dashboards that showcase Shield’s tangible impact on reducing incidents, improving response times, or meeting compliance standards. Automated reports can highlight changes over time, such as the reduction in unauthorized access attempts or incidents that were successfully blocked. These measurable outcomes provide concrete evidence that reinforces Shield’s value and encourages continued support.
- Risk Assessment and Scenario Planning: Show leadership the specific risks that Shield mitigates by conducting a risk assessment tailored to your organization’s Salesforce environment. Use real-world examples or “what-if” scenarios to illustrate how Shield could prevent significant incidents, particularly those relevant to your industry. This approach helps stakeholders visualize Shield’s role in protecting critical assets and understand the practical importance of these protections.
- Alignment with Strategic Objectives: Connect Shield’s value to the organization’s broader goals, such as customer trust, regulatory compliance, or business continuity. By framing security as a core component of business stability and reputation, security leaders can demonstrate how Shield supports organizational priorities. For example, highlight how Shield’s monitoring capabilities can reduce downtime, which directly supports business continuity and customer satisfaction.
Conclusion: Overcoming Challenges with the Right Tools and Mindset
Salesforce Shield is a vital tool for protecting sensitive data and ensuring compliance within Salesforce environments. Although challenges like log complexity, integration fatigue, and balancing security with business continuity can arise, Shield’s value is fully realized when combined with the right tools and a proactive strategy.
For organizations looking to strengthen their Salesforce security, combining Shield with advanced monitoring solutions offers a powerful advantage. This integrated approach turns complex security data into practical insights, safeguarding your Salesforce environment and driving efficiency.
Discover how pairing Salesforce Shield with Sonar can help your organization protect its data, enhance productivity, and stay audit-ready—try Sonar free today to experience the benefits firsthand.
FAQs:
- What types of data can Salesforce Shield’s Event Monitoring track?
Salesforce Shield’s Event Monitoring can track a wide variety of user activities within your Salesforce environment, including login attempts, data modifications, API calls, and system performance. It helps you monitor critical security and performance metrics by giving you detailed insight into who is accessing your data, what they are doing, and how your system is performing.
- How can I make event monitoring logs more actionable for my team?
Event monitoring logs can feel overwhelming due to the sheer volume of data. To make these logs actionable, it’s essential to use tools like Sonar that can transform raw logs into visual insights and provide real-time alerts. By doing so, you enable your team to focus on the most critical security events without having to manually sift through endless logs.
- Is Salesforce Shield difficult to integrate with existing tools and processes?
While integrating Salesforce Shield may require initial configuration, it is designed to work smoothly within the Salesforce ecosystem. Tools like Sonar can help by centralizing monitoring across your entire tech stack, simplifying integration processes, and reducing the burden on your team. This ensures that event monitoring works seamlessly with your current operations.
- How does Salesforce Shield help with regulatory compliance?
Salesforce Shield’s Event Monitoring, along with its other features like Platform Encryption and Field Audit Trail, helps businesses meet compliance requirements for regulations such as GDPR, HIPAA, and PCI-DSS. It offers detailed tracking of data access and modifications, enabling your team to conduct audits and ensure data security. Tools like Sonar enhance these capabilities by automating alerts and audits, further simplifying compliance efforts.
- How can I justify the cost of Salesforce Shield to my leadership team?
While Salesforce Shield may seem costly upfront, it ultimately helps reduce IT costs by up to 25% through proactive security and compliance measures. By preventing costly data breaches, minimizing downtime, and ensuring compliance, Salesforce Shield can save your organization from fines, lost revenue, and reputational damage. Using complementary tools like Sonar to automate monitoring and reporting can further enhance the ROI by streamlining processes and reducing the manual workload for your team.