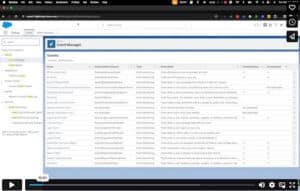
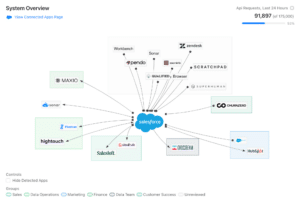
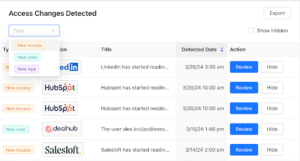
Are you operating on blind faith when it comes to Salesforce data security? IT & Operations leaders have a lot on their plate in terms of ensuring the security of their organizational tech stack. From managing user profiles and permissions to data encryption and ensuring regular backups, there’s no shortage of responsibilities.
Amidst this busy scene, Salesforce’s expansive list of integrated tools often gets overlooked. But with third-party SaaS applications racing to introduce AI into their integrated offerings, and with integrated system ownership spread across business units… Salesforce can introduce significant risks to your organization.
A primary threat to your third-party security management for Salesforce comes from system misconfiguration. In fact, Gartner points out that by 2025, 99% of data leaks will be due to preventable misconfigurations or user errors. Even if an integration was configured appropriately at the start, over time, changes are introduced that cause them to fall out of compliance. And there’s simply not enough time to manually monitor every new integration by GTM teams, opening up vulnerabilities and complicating data governance and compliance. That’s why it’s critical for InfoSec leaders to work closely with their Salesforce Operations teams and invest in the appropriate resources to mitigate these risks before they escalate.
For any enterprise using Salesforce, a necessary investment to your information security program should be in Salesforce Shield. Released in 2015, Shield arms Operations teams with data encryption, expanded field audit trail, data detect and event monitoring tools. But Shield comes with a hefty price tag so it’s critical your team operationalizes it.
While Salesforce includes Event Monitoring in its Shield offering, Ops leaders are struggling to find easy or obvious ways to proactively integrate it with their third party security management programs. Below, we’re covering all your FAQ’s regarding Salesforce’s Event Monitoring. What is it? How do you know if you already have it? How do you enable it? How do you make the Event Monitoring data more actionable? Read on to get all the answers.
Top FAQs: Salesforce Event Monitoring Basics
Now that we’ve covered the significance and potential of Salesforce Event Monitoring, let’s dive deeper into the fundamentals to add clarity to how users can use this tool most effectively.
1. What is Event Monitoring?
Salesforce Shield’s Event Monitoring is a powerful feature that gives you a comprehensive view into the granular details of user activity within your Salesforce environment. At its core, Event Monitoring enables administrators and IT leaders to track and analyze a wide array of events that occur across the Salesforce platform, including but not limited to login attempts, report views, data exports, and changes to records or configurations.
2. What is Salesforce Event Monitoring used for?
Salesforce Event Monitoring is used for a variety of things including:
- Security: By monitoring login patterns and access attempts, your team can quickly identify and respond to unauthorized or suspicious behavior, helping to prevent potential security breaches before they happen.
- Compliance: Event Monitoring supports compliance efforts by providing detailed audit trails of user actions. This makes it easier for your team to adhere to industry regulations and standards, as you can demonstrate who accessed what data, and when.
- Performance optimization: Understanding how users interact with Salesforce applications can highlight areas where the system or processes could be optimized for better performance. For example, tracking which reports are run most frequently can help in prioritizing system resources or identifying training needs.
- User adoption and engagement: By analyzing how users are engaging with Salesforce, you can identify areas where user adoption may be lagging or where additional training might be needed, ensuring that the investment in Salesforce is fully leveraged.
Event Monitoring data is accessible through various means, including API access for custom analytics or integration with third-party monitoring tools, as well as through Salesforce’s own reporting and dashboard capabilities. This provides a flexible and powerful toolkit for you and your team to ensure that your Salesforce environment is secure, compliant, efficient, and effectively utilized.
3. Who would find Salesforce Event Monitoring valuable?
Event Monitoring within Salesforce Shield is a pivotal resource for various teams throughout an organization, enhancing their ability to maintain security, compliance, operational efficiency, and system integrity.
- Operations (Ops) team: For the Ops team, Event Monitoring is a cornerstone for ensuring that Salesforce and its integrated applications are functioning as expected. This team leverages the insights gained from monitoring to identify and address operational issues, optimize system performance, and refine business processes. The goal is to enhance productivity and user experience, ensuring that the organization’s operations are running smoothly and efficiently.
- IT and Business Systems owners: The IT and business systems team values Event Monitoring for its role in safeguarding the technical stack’s health and functionality. It provides a means to detect any integration issues or system malfunctions early, allowing for swift resolution. This team is also responsible for implementing changes within the Salesforce environment. Thus, Event Monitoring aids them in understanding the impact of these changes, facilitating effective change management and risk mitigation to maintain seamless business operations.
- Information security (InfoSec) and data governance team: For InfoSec and data governance teams, Event Monitoring is critical for security oversight and regulatory compliance. It enables them to monitor for security threats, unauthorized access, and potential data breaches, ensuring that sensitive information is protected. Furthermore, these teams rely on Event Monitoring to uphold compliance with data protection regulations and governance policies like HIPAA, GDPR, PCI DSS, etc. By providing detailed audit trails and logs of user activities, Event Monitoring assists in enforcing strict data usage and access standards, vital for maintaining the organization’s integrity and trust.
4. What Salesforce package is Event Monitoring included with?
Salesforce Event Monitoring is part of the Salesforce Shield suite, which is a premium set of security tools designed to enhance data security, compliance, and governance across Salesforce applications.
Salesforce Shield, including Event Monitoring, is not included with the standard Salesforce packages and requires an additional purchase. Organizations looking to leverage Event Monitoring for detailed insights into user behavior, application performance, and security threats must subscribe to Salesforce Shield on top of their existing Salesforce license.
5. What level of Salesforce service do I need to get Event Monitoring?
Salesforce Event Monitoring is available as part of the Salesforce Shield platform, which is an additional add-on to certain Salesforce editions.
The following packages support Salesforce Shield:
- Salesforce Enterprise Edition with Performance, Unlimited, or Developer editions
- Salesforce Health Cloud
- Salesforce Financial Services Cloud
6. Do I have to buy Salesforce Shield in order to get SF Event Monitoring?
While part of the Shield suite of security features, Salesforce allows you to purchase Event Monitoring – typically priced at 10% of your total Salesforce contract.
7. How do I identify if my current package already has Event Monitoring?
To access important information regarding installed packages, go to setup, enter “Installed Packages” in the Quick Find box, select “Installed Packages,” and then click on the name of the package for more detail.
8. How do I enable Salesforce Event Monitoring?
To enable Salesforce Event Monitoring, first make sure your org has purchased Salesforce Shield.
Then, navigate to Setup and access Event Monitoring settings by searching for “Event Monitoring setup” in the quick find box.
Within the settings, enable the “event log file” feature to start logging events. Configure the retention settings for event log files according to your org’s specific need. Once enabled, Salesforce will start logging events, allowing teams to monitor and analyze activity.
9. How much does Event Monitoring cost?
Salesforce Shield pricing varies depending on factors such as the edition of Salesforce you have and the specific features you require, but pricing is typically 30% of your total contract value. Event monitoring can be purchased ala carte at 10% of your net spend.
10. Is there trial access to Salesforce Event Monitoring?
Salesforce can provide you with a demo of the Salesforce Shield suite. You may also be able to request a courtesy license from your Salesforce account executive, typically available for a 30 day trial.
11. I purchased Salesforce Event Monitoring. Now what?
At first glance, it can be difficult to understand how to utilize the data Event Monitoring provides you and your team. So, how do you get started?
Use cases
In terms of how to utilize Event Monitoring as you get started, there are a variety of use cases:
- Security analysis and breach detection: Detect unauthorized access and potential security breaches by monitoring login attempts, record access, and export activities.
- How to get started: Set up alerts for unusual login patterns (e.g., off-hours access, failed login attempts) to quickly investigate and respond to potential threats.
- Compliance and audit trails: Maintain compliance with regulatory standards by providing detailed audit trails of user actions, such as data views, edits, and deletions.
- How to get started: Generate reports on user activities to support compliance audits, ensuring that data handling meets regulatory requirements.
- Performance optimization: Improve Salesforce performance by analyzing user activity data to identify bottlenecks or inefficient processes.
- How to get started: Use event log files to pinpoint slow-running reports or dashboards, then optimize these elements to enhance system performance.
- User adoption and engagement: Gauge user adoption and engagement by tracking how users interact with Salesforce, including which features or applications are most used.
- How to get started: Analyze usage patterns to identify areas where additional training or user support may be needed, enhancing overall productivity and system value.
- Data governance: Enforce data governance policies by monitoring data access and sharing within Salesforce.
- How to get started: Review access logs and changes to data sharing settings to ensure sensitive information is appropriately protected and shared.
How Event Monitoring data is presented and received
Event Monitoring data is collected and stored in Event Log Files (ELF), which are detailed logs of various user activities and system events within Salesforce. These logs are typically available within 24 hours of the event occurrence and can be accessed for up to 30 days.
4 Gaps in Salesforce’s Event Monitoring & How to Enhance It
One of the biggest problems with the logs provided by Salesforce’s Event Monitoring tool is that it can be difficult to know what to do with it… it’s just data that has no context and no action items. For this reason, Salesforce’s out-of-the-box Event Monitoring tool can create gaps– hindering the ROI you want from your Shield investment. We’re going into detail about the gaps and challenges that come with Event Monitoring, plus how Sonar Pulse can patch these holes and help maximize your Shield investment.
1. Limited integration and tech stack monitoring
Without integration capabilities, Event Monitoring focuses solely on Salesforce activities, leaving out insights of other interconnected systems. This isolation leads to fragmented data, making it challenging to correlate events across platforms and understand the full picture of IT operations.
This gap can cause orgs to miss critical performance, security, and compliance insights and increases risk across the board.
How Sonar Pulse solves this: To combat this risk, Sonar Pulse provides observability across integrated apps by combining monitoring efforts with proactive threat detection, allowing your team to discover and resolve issues quickly.
2. Reactive rather than proactive data loss prevention
Waiting for incidents to happen means delays in spotting and tackling data breaches. This leaves sensitive data ripe for compromise. Plus, it’s a costly game to lose, with higher expenses for incident response and potential reputation damage. With limited prevention capabilities in Salesforce Event Monitoring, orgs are left vulnerable.
How Sonar Pulse solves this: Sonar Pulse switches gears with proactive measures, like real-time monitoring and predictive analytics, to pinpoint any potential risks before they happen.
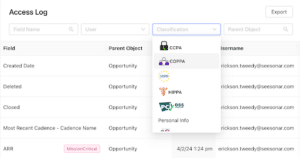
3. Inadequate capacity planning and resource management
Think performance bottlenecks, unexpected costs, and downtime risks. Without proper planning in place, orgs face user frustration, decreased productivity, and potential revenue loss. Plus, scalability can become a challenge and resource underutilization just adds fuel to the fire.
How Sonar Pulse solves this: If you’re looking to tighten up resource management for smoother operations, Sonar Pulse provides Systems leaders with insight to things like API consumption, license utilization, and CPU usage for more accurate forecasting and capacity planning.
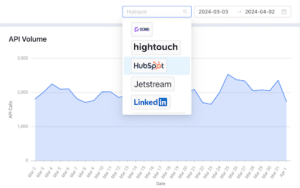
4. Absence of data lineage management
Without data lineage management, orgs lose visibility in data origin, movement, and transformations, raising accuracy and reliability concerns. Compliance quickly becomes a headache, with difficulty tracking down the root cause. A lack of data lineage management leads to data governance and management efforts falling short, ultimately impacting data quality.
How Sonar Pulse can solve this: Sonar enables teams to visualize where data is being accessed or managed across active integrations. By tracking data lineage, data security can remain uncompromised.
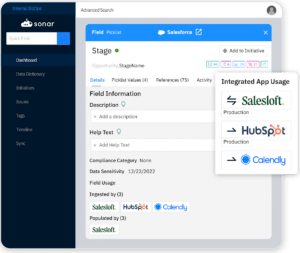
Conclusion: Make Sense of Your Event Monitoring Logs & Maximize Your Shield Investment with Sonar Pulse
Salesforce Event Monitoring is crucial to ensuring the security and compliance of your Salesforce environment. However, it’s essential that ops teams are aware of potential gaps in the system and have a full understanding of the Event Monitoring fundamentals.
With the increasing complexity of integrations, it’s easy for vulnerabilities to go unnoticed, posing significant security threats. Sonar Pulse serves as a powerful way to combat these gaps, providing comprehensive monitoring and protection.
Don’t let your Salesforce platform become a vulnerability – empower your team with the knowledge they need to stay ahead of threats and protect your data with Sonar Pulse. Try Sonar Pulse today!