Did you know that AI-driven cyber threats are projected to cost businesses over $10.5 trillion annually by 2025? And security leaders are preparing for AI attacks to be a daily occurrence at that point.
As AI makes waves across all industries and technologies, its potential to enhance productivity and insights is immense. However, the risks and need for heightened security cannot be overlooked.
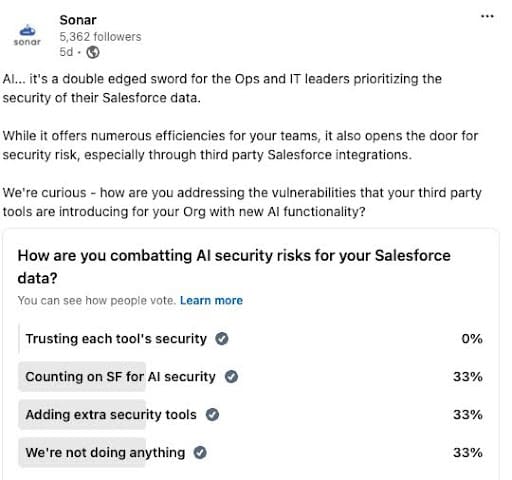
While you’re busy building security procedures, training your workforce and upgrading your cybersecurity solutions to meet regulatory requirements, one area often overlooked is your Salesforce Org. In fact, in a recent LinkedIn poll, we found that 33% of teams aren’t doing anything to address AI security risk within Salesforce.
As a security leader, it’s crucial to understand that while Salesforce excels at protecting your CRM data from AI security threats, your broader integrated tech stack may expose you to risks that your team and tools might not detect until it’s too late.
In this blog, we’re diving into exactly that. You’ll discover:
- Salesforce’s commitment to AI data security: How they’re enhancing protection measures and addressing your biggest AI security concerns.
- Gaps and risks from third-party integrations: Why these integrations might not follow the same stringent AI security protocols as Salesforce, creating potential vulnerabilities.
- Practical steps for mitigating risk: How you can prepare your teams and infrastructure to ensure your CRM data remains safe and sound, despite the complexities introduced by AI.
Let’s explore how Salesforce is navigating the AI landscape to keep your data secure… and what you can do to stay one step ahead.
How AI Can Expose Risk to Salesforce Data Security
Implementing AI can be a double-edged sword… On one side, AI-powered tools are enhancing our ability to detect and prevent cyber threats. Yet, the same technology is being exploited to lower the barriers for cybercriminals. These malicious actors are using AI to craft sophisticated phishing campaigns, develop advanced hacking tools, and commit credit card fraud. AI can write malicious code, identify system vulnerabilities, and create elusive malware, expanding the potential for cyber attacks on Salesforce and other platforms. Here are some ways AI may put your Salesforce data at risk:
1. Evolved Phishing Strategies
Phishing attacks have become more sophisticated and widespread. No longer confined to email, attackers now use public-facing applications to extend their reach. These new tactics make phishing a more pervasive threat in the digital landscape. In 2023, hackers exploited a zero-day vulnerability in SMTP servers and Salesforce email services to execute a phishing campaign targeting Facebook accounts.
2. Limited Threat Visibility
One of the biggest challenges for companies using Salesforce is the lack of visibility into potential cyber threats. Without robust threat detection and malware scanning capabilities across their Org and its integrated tech stack, organizations are at increased risk of attack. Salesforce does not inherently offer comprehensive visibility into cyber threats within the system, leaving companies to devise their own solutions. Visibility is the cornerstone of a strong security strategy, and its absence can leave significant gaps in protection.
3. Rising Ransomware Threats
Your Salesforce data is currency to hackers. As such, ransomware attacks are a growing concern, capable of causing extensive damage through downtime, system disruptions, financial loss, and legal complications. As attackers become more sophisticated, companies need proactive security measures to safeguard their Salesforce environments. Failure to do so can result in devastating consequences, underscoring the need for a forward-thinking approach to cybersecurity.
4. Addressing Configuration Vulnerabilities
By 2025, 99% of data leaks will be due to misconfiguration and user errors. Even minor configuration errors can lead to serious security breaches. Reports have shown that misconfigured Salesforce settings can grant unauthorized access to sensitive data. These vulnerabilities often stem from default settings that provide excessive access. This heightens the need for security leaders to have their finger on the pulse of who has access to Salesforce data and what kinds of data. Having this kind of visibility requires the right tools that allow security leaders to configure settings properly and disable unnecessary external sharing and user permissions at any given time.
Salesforce’s Commitment to Data Security
With the implementation of AI, Salesforce is tackling security concerns and challenges like accuracy, bias, and privacy head on. As companies rush to harness AI for productivity gains, maintaining trust is at the forefront of Salesforce’s priorities. The platform is dedicated to keeping your data secure as AI becomes more embedded in its ecosystem. Here’s how they’re demonstrating that commitment:
1. Responsible AI Development
To address trust concerns, Salesforce introduced five guidelines for responsible generative AI development. These guidelines emphasize transparency, accountability, and ethical use of AI, helping mitigate the risks associated with new technology.
Additionally, Salesforce advocates for tailored, risk-based AI regulations that consider the context and use of the technology. For example, while developing a generative AI chatbot to teach cooking might require fewer guardrails, AI applications in finance demand rigorous oversight and PCI DSS compliance. This tailored approach ensures that high-risk applications receive the necessary scrutiny, while still allowing for innovation in lower-risk areas.
Here are the key principles of Salesforce’s approach to responsible AI:
- Risk-based framework: Salesforce supports regulations focusing on high-risk AI applications, particularly those with significant legal, financial, or ethical implications. This ensures the most critical areas receive the necessary protection.
- Contextual differentiation: Salesforce believes that AI regulation should vary based on the context and specific use of the technology. Developers and users of AI must be accountable for how the technology is implemented and governed. This means that the end-users, your Ops team, and your security team need to be aligned on data security practices.
- Data privacy laws: Protecting data privacy is fundamental. Salesforce advocates for rules that address the use and privacy of personal data in AI training, ensuring individuals’ rights are safeguarded.
- Transparency: AI systems should operate transparently, allowing users to understand the decision-making processes behind AI recommendations. It’s crucial for individuals to know whether they are interacting with a human or an AI system.
- Accountability and oversight: Implementing AI impact assessments and risk management frameworks helps promote accountability and compliance. Salesforce supports a balanced approach that maintains market entry, competition, and innovation while ensuring responsible AI use.
- Harmonization with existing rules: Salesforce believes new AI regulations should align with existing laws and policies to avoid redundancy and ensure coherence.
- Future-proof regulations: AI regulations should be globally interoperable, durable, and flexible, providing a framework that can adapt to the rapid pace of technological advancement.
2. Einstein GPT
At the forefront of Salesforce’s AI initiatives is Einstein GPT, the world’s first generative AI for customer relationship management (CRM). Einstein GPT is designed to leverage AI’s productivity gains while ensuring robust data security. Key features of Einstein GPT include:
- Dynamic grounding: This feature ensures that the AI provides responses based on accurate, up-to-date information, preventing AI from generating incorrect or misleading content.
- Data masking: Sensitive data is replaced with anonymized information to protect privacy and comply with data protection regulations.
- Toxicity detection: AI outputs are scanned for harmful content, ensuring that interactions remain appropriate and professional.
- Zero retention: Customer data is never stored outside Salesforce, ensuring that generative AI prompts and outputs are not retained or learned by the model.
3. Engaging with Global Stakeholders
Salesforce is also actively engaging with governments, industry, academia, and civil society to develop and promote responsible AI norms. This includes participation in global initiatives and advisory committees focused on ethical AI use.
The Reality of Third-Party Integrations
There’s no denying that Salesforce itself is committed to protecting your data while simultaneously leveraging AI to improve the efficiency of your teams. But as much as the platform is doing to build an AI-safe framework within their tools… There are some things that go beyond their control. Where hidden risks creep in are through your integrated tech stack. Third-party tools can open the doors for:
- Data leakage: Transferring data between systems increases the risk of unauthorized access or data breaches. Sensitive information might be exposed during the integration process, especially if the third-party application lacks robust security measures.
- Inconsistent security protocols: Not all third-party applications adhere to the same stringent security standards as Salesforce. This inconsistency can create weak points in your security framework, making your data more susceptible to cyberattacks.
- Authentication and authorization risks: Integrations often require sharing authentication credentials or API keys, which, if not managed securely, can be compromised. Weak authentication mechanisms in third-party apps can lead to unauthorized access to Salesforce data.
- Compliance issues: Different applications may have varying levels of compliance with data protection regulations like GDPR or CCPA. Using third-party integrations that do not comply with these standards can result in legal ramifications and hefty fines.
- Data integrity concerns: Ensuring that data remains accurate and unaltered during and after the transfer process is critical. Misconfigured integrations can lead to data corruption or loss, impacting business operations and decision-making.
Going Beyond Salesforce’s Build in Security
While Salesforce is committed to maintaining robust security within its platform, it cannot control the security practices of third-party tools. Each integration introduces unique risks, especially concerning how these tools handle AI and data security. Additionally, Salesforce doesn’t provide the infrastructure to offer a holistic view of data and access controls across your entire integrated tech stack, making it incredibly hard to know when a breach occurs before it’s too late. This lack of visibility and control can make it challenging to manage and secure data effectively.
Below, we’re giving proactive tips for how you can protect your Salesforce org in ways Salesforce itself cannot.
1. Vetting third-party tools
Before integrating any third-party tools with Salesforce, it’s essential to thoroughly vet them. Here’s what to look for:
- Security certifications: Ensure the tool has industry-standard security certifications such as ISO 27001, SOC 2, or GDPR compliance.
- Data handling policies: Review how the tool handles data, including storage, encryption, and access control practices.
- Reputation and reviews: Look for feedback from other users and industry experts. Tools with a good track record are less likely to have security flaws.
- Vendor security practices: Assess the vendor’s overall security practices, including how they manage updates, patch vulnerabilities, and handle incidents.
2. Invest in Salesforce Shield Event Monitoring
Another critical step in securing your Salesforce data is investing in Salesforce Shield’s Event Monitoring. This powerful tool offers several benefits:
- Detailed insights: Event Monitoring provides detailed logs of all user activity within your Salesforce org. This helps you track who accessed what data, when, and from where.
- Anomaly detection: By monitoring events in real-time, you can detect unusual patterns or behaviors that might indicate a security threat.
- Compliance support: Event Monitoring helps you comply with data protection regulations by providing the necessary audit trails and activity logs.
- Enhanced visibility: Gain a comprehensive view of your data interactions, which is crucial for identifying potential security breaches quickly.
3. Amplify Salesforce Shield with Sonar Pulse
Shied is a fantastic investment, but some teams struggle to make proactive security plans from its existing log-UX format. Sonar Pulse takes your event monitoring data from Salesforce Shield and transforms it into actionable insights. With real-time analysis and visualization of access logs, Sonar Pulse helps you track integrated applications, monitor for changes, and observe API activity. This added layer of observability ensures you can detect and address security issues before they become critical. Pulse fills in gaps for Salesforce by providing you:
- Holistic data visibility: Sonar Pulse provides a comprehensive view of data across all integrated platforms, helping you detect anomalies and potential breaches early.
- Proactive issue detection: It continuously monitors for potential issues, ensuring that you can address security threats before they escalate.
- Enhanced access controls: With Sonar Pulse, you can implement more granular access controls, ensuring that data is only accessible to those who truly need it.
By integrating Sonar Pulse with Salesforce Shield, you can maximize your security investment, elevate your Salesforce security, and ensure data security is at the forefront of your GTM team’s minds.
Conclusion: Take Salesforce Data Security Into Your Own Hands
As AI becomes more prevalent, cyber threats are becoming increasingly sophisticated. For security leaders, protecting your Salesforce data requires a proactive and comprehensive approach. AI technology holds immense potential to enhance productivity and insights, but it also brings significant security challenges that must be addressed.
While Salesforce is dedicated to protecting your data, their reach can’t expand beyond the CRM itself, requiring you to implement the safeguards necessary to ensure data is protected at all times.
With Sonar Pulse, you can have visibility into how information is flowing between Salesforce integrations, when an unexpected change causes it to be interrupted, and where it exposes you to risk. Try the ultimate Salesforce data security software, Sonar, today. Request a demo here.

